Business Development Manager, Alan Suyko notes that the key information in this summarised HID Global article relate to:
• Knowing more about access technologies work and how this can help you evaluate your choices
• Learning to better understand how the process of mutual authentication works
• Exploring the four common elements of an access control solution and how they interact
The Four Elements of a Physical Access Control System
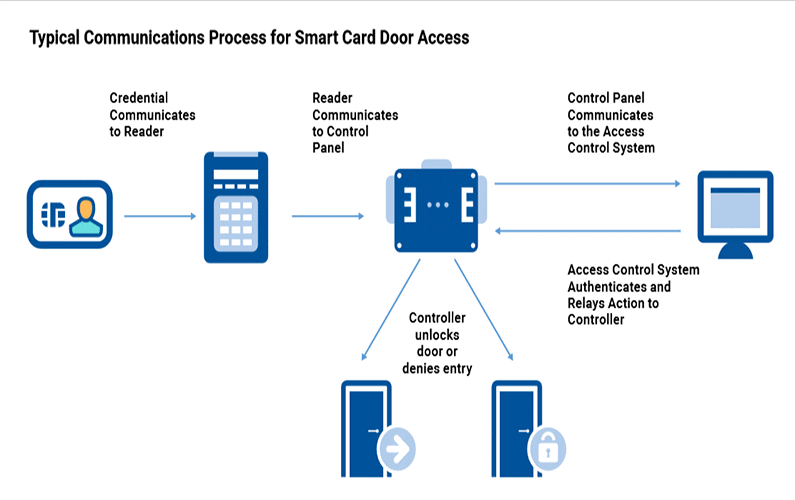
Most physical access control systems consist of four basic elements. Depending on the size and purpose of the system, there may be additional devices, but generally, the four basic elements are:
1. Credentials
2. Readers
3. Controllers
4. Host
1. Credentials
Almost all physical access credentials carry a number, or set of numbers that are used to identify the holder. This most often takes the form of a simple string of binary numbers (ones and zeros) often referred to as the “payload.” Manufacturers will program and personalize credentials capable of carrying this kind of binary data onto a form factor (e.g., Smart Card, fob, mobile device, etc.).
The way data is conveyed to the reader varies according to the technology involved. In every case, however, the “payload” is a string of binary numbers of some fixed configuration and length. The way this data is configured is called the format. The credential itself has no awareness of the makeup of its format, nor is it aware of any access privileges for the cardholder. That information exists only at the panel and host software.
Common Credential Technologies Found in Access Control Applications
The technologies commonly found in access control credentials deployed today include:
• Magnetic Stripe (Legacy Technology)
• Low Frequency 125 kHz (Legacy Technology)
• High Frequency 13.56MHz (Current standard)
• Ultra High Frequency
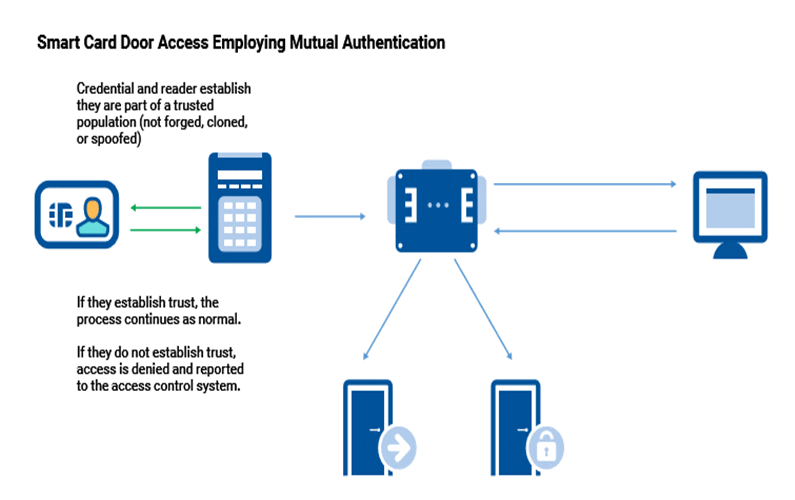
Credential & Reader Mutual Authentication
To protect against common vulnerabilities, including forgery, cloning, and spoofing, some contactless smartcards and mobile credentials have an additional security step called “mutual authentication” that is completed before the binary data can be extracted from the credential.
2. Readers
Readers can be configured to read only the credentials in the respective cardholder population. Some are designed to support just one technology, but some support a vast array of multitechnology configurations.
A configuration is a set of physical reader attributes and capabilities combined with programming options to suit the reader application.
Typical reader configuration options include:
• What credential types can be read
• Type of encryption used
• LED and beeper behavior
• Whether there is a keypad
• When a credential is read
• When the optical tamper switch is enabled
3. Controllers
When the controller receives the data from the reader, its embedded firmware begins the process of deciding whether or not to grant access.
4. Host
Every access control system has some form of user interface, usually a discrete PC application or web-based interface for operators to interact with the system.
They will use it to:
• Add and delete cardholders
• Assign, modify or delete access privileges
• Create and modify time schedules, holiday lists, etc.
• Configure system hardware for doors, alarm points, etc.
• Monitor system events in real time
• Generate historical reports on all types of system activity
For more detail, see the PDF download on the left.
Important Takeaways….
• Adopting current industry standard over legacy technology is beneficial and reduces risk
• Solutions offering mutual authentication between reader and credential offer additional protection against cloning, spoofing and forgery, particularly for multi-purpose credentials
• In most cases, the controller is the only device in the system where the binary card data format can be decoded and acted upon. Understanding controller capabilities will give you greater insight into how your system will perform with any given credential technology
• The host system is where access control rights are managed and maintained
Online Information:
Glyn Contact:
Need more information? Want to know about our extensive reference designs and engineering services?
- Email us at sales@glyn.com.au
- Call the sales team in Australia here and New Zealand here